
February 29, 2016 Apple wins in New York as judge declines to force them to comply with All Writs Act. This update Start of the Story Tweet
February 29, 2016
 Apple not alone with problems in handling time changes. The International Date Line repulsed F-22 Raptor air supremacy fighters enroute to Kadena AFB forcing return to Hickam AFB. Story Tweet
Apple not alone with problems in handling time changes. The International Date Line repulsed F-22 Raptor air supremacy fighters enroute to Kadena AFB forcing return to Hickam AFB. Story Tweet
February 29, 2016  SnapChat CEO to payroll: Send me information, including SSNs, on our employees. Done! Problem? Yeah, it wasn’t the CEO, but a spear-phisher. Don’t take unusual actions based on incoming communications. Story Tweet
SnapChat CEO to payroll: Send me information, including SSNs, on our employees. Done! Problem? Yeah, it wasn’t the CEO, but a spear-phisher. Don’t take unusual actions based on incoming communications. Story Tweet
February 29, 2016  Did we expose ourselves? Did US intelligence services create backdoors in US-made networking equipment? Did what we gain pale compared to what others grabbed on a larger scale? Story Tweet
Did we expose ourselves? Did US intelligence services create backdoors in US-made networking equipment? Did what we gain pale compared to what others grabbed on a larger scale? Story Tweet
February 29, 2016 It used to be if a computer wasn’t connected to the internet it was safe, isolated by what was termed the “air gap” between systems. No more. Story Tweet
February 28, 2016  eFiling? Beware, some big names don’t do well in protecting your information. Story Tweet
eFiling? Beware, some big names don’t do well in protecting your information. Story Tweet
February 28, 2016  iPhone users – fingerprint scanner spoofed with PlayDoh, really. Story Section on Biometric Security Tweet
iPhone users – fingerprint scanner spoofed with PlayDoh, really. Story Section on Biometric Security Tweet
February 28, 2016  Researcher finds unsecured database with kid info including location, texts, images. Tells company who secures database rapidly then excoriates the researcher. Company gets FTC/COPPA violation and displays really poor manners. Story Tweet
Researcher finds unsecured database with kid info including location, texts, images. Tells company who secures database rapidly then excoriates the researcher. Company gets FTC/COPPA violation and displays really poor manners. Story Tweet
February 27, 2016  Is your hospital focused on protecting you or your data? A two year study, including benign attacks on a dozen facilities were analyzed and the results made into actionable guidance for hospitals to improve security for you! Story Tweet
Is your hospital focused on protecting you or your data? A two year study, including benign attacks on a dozen facilities were analyzed and the results made into actionable guidance for hospitals to improve security for you! Story Tweet
February 27, 2016  Financial information for 80,000 students, staff, and vendors were exposed in a hack of the financial systems at University of California at Berkely. Story Tweet
Financial information for 80,000 students, staff, and vendors were exposed in a hack of the financial systems at University of California at Berkely. Story Tweet
February 27, 2016  Update: iPhone users: The 1970 bricking has a wider date range. The good news: next iOS should prevent it. For brick recovery see this update Start of the Story Tweet (Delay due to blizzard re privacy vs surveillance sorry!)
Update: iPhone users: The 1970 bricking has a wider date range. The good news: next iOS should prevent it. For brick recovery see this update Start of the Story Tweet (Delay due to blizzard re privacy vs surveillance sorry!)
February 26, 2016  PII for 10M California kids is about to be released, with weak security, to lawyers.What could possibly go wrong? Story Tweet
PII for 10M California kids is about to be released, with weak security, to lawyers.What could possibly go wrong? Story Tweet
February 26, 2016 IRS raised number affected. May 2015:100k. August 2015:344k. February 2016:700k. Any more? What took so long? This update Start of the story Tweet
February 25, 2016  Multiple updates in the Surveillance vs Privacy case between the FBI and Apple. Bill Gates clarifies position vs what was reported by media Update Can Apple be compelled to write code? Update At least one Congressman agrees with Apple Update Would this set a new precedent? If so, is that precedent justified? Update Apple is creating a new and more secure iPhone. Update Start of the Story Tweet
Multiple updates in the Surveillance vs Privacy case between the FBI and Apple. Bill Gates clarifies position vs what was reported by media Update Can Apple be compelled to write code? Update At least one Congressman agrees with Apple Update Would this set a new precedent? If so, is that precedent justified? Update Apple is creating a new and more secure iPhone. Update Start of the Story Tweet
February 25, 2016  Nissan Leaf App found to have near-zero access controls allowing internet control over many functions. Nissan told months ago. Story Update 1: App Disabled Update 2: Not Everywhere Tweet
Nissan Leaf App found to have near-zero access controls allowing internet control over many functions. Nissan told months ago. Story Update 1: App Disabled Update 2: Not Everywhere Tweet
February 24, 2016  Good news: New employee got a whiff of something bad, got a confirming sniff and stopped a compromise. Story Tweet
Good news: New employee got a whiff of something bad, got a confirming sniff and stopped a compromise. Story Tweet
February 23, 2016  In their court papers and press releases the DOJ & FBI have repeatedly referred to their request of Apple as a one-time event. Records unsealed in another court show this is just their most recent request. This Update Start of the Story Tweet
In their court papers and press releases the DOJ & FBI have repeatedly referred to their request of Apple as a one-time event. Records unsealed in another court show this is just their most recent request. This Update Start of the Story Tweet
February 23, 2016  San Berdardino officials were acting at request of FBI in attempting a reset. MotionToCompel indicated RemotePasswordChange was completed, but MDM software had not been installed. How? What? Who? Story Tweet
San Berdardino officials were acting at request of FBI in attempting a reset. MotionToCompel indicated RemotePasswordChange was completed, but MDM software had not been installed. How? What? Who? Story Tweet
February 23, 2016 OPM Info Chief resigns and her appearance before Congress gets canceled. Will we ever learn what happened from the inside perspective? This Update Start of the Story Tweet
February 22, 2016  Multiple events: A respected researcher: this is a headlong leap into a bad place. Story FBI press release Story Apple letter describing past, requests of them in the present, what it means for the future and apparent acceptance of invitation to move from Judiciary to Legislative branch of government. Story Start of the Story Tweet
Multiple events: A respected researcher: this is a headlong leap into a bad place. Story FBI press release Story Apple letter describing past, requests of them in the present, what it means for the future and apparent acceptance of invitation to move from Judiciary to Legislative branch of government. Story Start of the Story Tweet
February 22, 2016  Linux Mint update: How hack was done, very limited exposure, forum compromised, beware spear-phishing. This Update Start of the Story Tweet
Linux Mint update: How hack was done, very limited exposure, forum compromised, beware spear-phishing. This Update Start of the Story Tweet
February 21, 2016  Apple mobile device management (MDM) would have remotely unlocked phone and done a lot more. The county paid for it, but apparently never installed it. This Update Start of the Story Tweet
Apple mobile device management (MDM) would have remotely unlocked phone and done a lot more. The county paid for it, but apparently never installed it. This Update Start of the Story Tweet
February 21, 2016  Becoming a target is a price you pay for being a leader in Linux distributions. Linux Mint was hacked and malware installed in the distribution. Excellent communication and response by the organization. Story Tweet
Becoming a target is a price you pay for being a leader in Linux distributions. Linux Mint was hacked and malware installed in the distribution. Excellent communication and response by the organization. Story Tweet
February 20, 2016  Update: re Apple v FBI. It isn’t the murderer’s passcode that needs cracking. The iPhone 5C passcode was changed after it was in the custody of law enforcement. This Update Start of the Story Tweet
Update: re Apple v FBI. It isn’t the murderer’s passcode that needs cracking. The iPhone 5C passcode was changed after it was in the custody of law enforcement. This Update Start of the Story Tweet
February 20, 2016  Two epic failures adding to the Inherent Danger on the Internet of Things. One is a home security system that radiates its PIN without encryption and you can’t update it. Story. The other a DVR that sends still images around the world and you can’t stop it. Story. Tweet
Two epic failures adding to the Inherent Danger on the Internet of Things. One is a home security system that radiates its PIN without encryption and you can’t update it. Story. The other a DVR that sends still images around the world and you can’t stop it. Story. Tweet
February 19, 2016  In the fray between the FBI and Apple, now comes cybersecurity legend John McAfee with an offer to obtain access the phone so Apple does not need to weaken security for all of us. IMO … This Update Start of the Story Tweet
In the fray between the FBI and Apple, now comes cybersecurity legend John McAfee with an offer to obtain access the phone so Apple does not need to weaken security for all of us. IMO … This Update Start of the Story Tweet
February 19, 2016  Apple users: Protect your privacy. Defeat brute force attacks or delay them for years. See the simple technique and the math behind it. Story Tweet
Apple users: Protect your privacy. Defeat brute force attacks or delay them for years. See the simple technique and the math behind it. Story Tweet
February 19, 2016  Update; 10:06am Pacific Time – After just three days prosecutors file motion for judge to “compel” Apple to “comply”. Is that calm or kerosene on the fire? What says her Honor? This Update Start of the Story Tweet
Update; 10:06am Pacific Time – After just three days prosecutors file motion for judge to “compel” Apple to “comply”. Is that calm or kerosene on the fire? What says her Honor? This Update Start of the Story Tweet
February 19, 2016  Update: Apple v FBI. Why is the DOJ making this effort now? Waiting for a truly evil target that would gather little sympathy? Or, was there a concerted effort to crack security of crooks and citizens alike? This update Start of the Story Tweet
Update: Apple v FBI. Why is the DOJ making this effort now? Waiting for a truly evil target that would gather little sympathy? Or, was there a concerted effort to crack security of crooks and citizens alike? This update Start of the Story Tweet
February 18, 2016 Update to Apple vs FBI. Additional information on privacy, opening more doors, liability loses focus, new liability, a reference work, and a perhaps in-applicable quote from one founder of our Nation. This Update Start of the Story Tweet
February 18, 2016 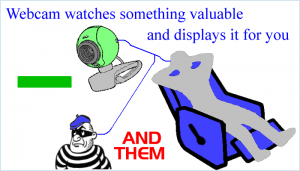 Would you hire a convicted embezzler to manage your funds? So why get a “security” device that works for crooks while it works for you? Knowledge is power, beware the Inherent Danger in the Internet of Things. Story Tweet
Would you hire a convicted embezzler to manage your funds? So why get a “security” device that works for crooks while it works for you? Knowledge is power, beware the Inherent Danger in the Internet of Things. Story Tweet
February 17, 2016 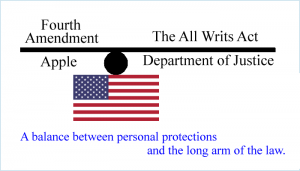 Facts, tools, considerations, implications and an opinion regarding privacy and cybersecurity for the smartphones of law-breakers as well as the law-abiding. Story Tweet
Facts, tools, considerations, implications and an opinion regarding privacy and cybersecurity for the smartphones of law-breakers as well as the law-abiding. Story Tweet
February 17, 2016 Update  Hollywood Presbyterian Medical Center paid the ransom and got a discount. Crooks unlocked files and all is well, for now. Story Tweet
Hollywood Presbyterian Medical Center paid the ransom and got a discount. Crooks unlocked files and all is well, for now. Story Tweet
February 16, 2016  Three hospitals hit with ransomware. One inconvenienced, two thrown back to 1970s-era capabilities. Urgent care moves further from critical patients. Prepared or not? Pay or not? Story Tweet
Three hospitals hit with ransomware. One inconvenienced, two thrown back to 1970s-era capabilities. Urgent care moves further from critical patients. Prepared or not? Pay or not? Story Tweet
February 16, 2016  This internet core function from November 2008 has a significant vulnerability that was publicly demonstrated just yesterday. What problems are out there that we don’t know? Story Tweet
This internet core function from November 2008 has a significant vulnerability that was publicly demonstrated just yesterday. What problems are out there that we don’t know? Story Tweet
February 16, 2016 According to Visa CEO Scharf just 17% of physical transaction merchants are EMV capable. Why so few? Was the purpose of EMV to protect consumers? Why are merchants and consumers unhappy? Story Tweet
February 16, 2016  A talking, flame shooting pumpkin on the internet of things. What could possibly go wrong? Story Tweet
A talking, flame shooting pumpkin on the internet of things. What could possibly go wrong? Story Tweet
February 16, 2016 Is the cloud a secure cyber storage place? Teacher: Maybe not so much. Certainly not the place to store … personal … pictures, videos, userids, passwords, address books etc. Story Tweet
February 15, 2016 The average age of a cyber-suspect is 17, but this 59 year old is keeping up the other end. Story Tweet
February 15, 2016 Did Angler bring you the new ransomware Hydracrypt or Umbrecrypt? Don’t pay! Read this for available decryption tools. Story Tweet
February 15, 2016 A UK court found that GCHQ can hack computers, phones etc. in the UK or abroad. Appears to accept intrusive nature with a balance. Other nations unhappy. So are a lot of people. Story Tweet
February 15, 2016 Voting Estonia stocks at Nasdaq are to be done using blockchain security which got a significant crack earlier this month. Story Tweet
February 14, 2016  Tweet @mastercard & @visa – tell them a better way exists that does not require new hardware for providers, merchants or consumers and adds functionality beyond anything available. See www.NC3.mobi Story Tweet
Tweet @mastercard & @visa – tell them a better way exists that does not require new hardware for providers, merchants or consumers and adds functionality beyond anything available. See www.NC3.mobi Story Tweet
February 14, 2016  The very bad MazarBot, the GCHQ and the NSA have what in common? One text message and your phone is theirs. You can stop one of them. Story Tweet
The very bad MazarBot, the GCHQ and the NSA have what in common? One text message and your phone is theirs. You can stop one of them. Story Tweet
February 14, 2016  Happy Valentine’s Day! An update to VTech who exposed 700,000+ children and 5,000,000 adults. “We’re Back!” and as a special thank you we’re shifting liability for future breaches over to you. Story Start of the story Tweet
Happy Valentine’s Day! An update to VTech who exposed 700,000+ children and 5,000,000 adults. “We’re Back!” and as a special thank you we’re shifting liability for future breaches over to you. Story Start of the story Tweet
February 11, 2016 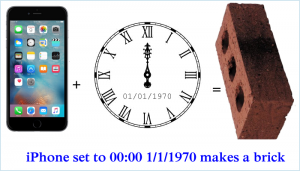 Are you kidding me? Another way to turn your iPhone into a brick just by setting an allowed time. There is good news, bad news, and really bad news. Story Tweet
Are you kidding me? Another way to turn your iPhone into a brick just by setting an allowed time. There is good news, bad news, and really bad news. Story Tweet
February 11, 2016  Crooks leverage your account to generate Kohl Cash at order time, then they trade KC for gift cards. You return the stuff when it gets to you. By then the crooks are long gone. Just the kind of crime NC3 was designed to defeat. Story Tweet
Crooks leverage your account to generate Kohl Cash at order time, then they trade KC for gift cards. You return the stuff when it gets to you. By then the crooks are long gone. Just the kind of crime NC3 was designed to defeat. Story Tweet
February 13, 2016  These days “security” and “Internal Revenue Service” seem to be words that don’t fit well together. Story Tweet
These days “security” and “Internal Revenue Service” seem to be words that don’t fit well together. Story Tweet
February 12, 2016  Two controlled tests running 8 and 30 hours on a Win10 machine with no user activity. In the least case Win10 connected to someone 90 times an hour. To who? What for? Story Tweet
Two controlled tests running 8 and 30 hours on a Win10 machine with no user activity. In the least case Win10 connected to someone 90 times an hour. To who? What for? Story Tweet
February 12, 2016  Surfing the net without adblocks is like eating fugu. You won’t die, but if you lose the gamble you might wish you had. A discussion on the need for AdRevenue vs ConsumerRisk. Story Tweet
Surfing the net without adblocks is like eating fugu. You won’t die, but if you lose the gamble you might wish you had. A discussion on the need for AdRevenue vs ConsumerRisk. Story Tweet
February 11, 2016  Good News: Google boots Flash. Story Tweet
Good News: Google boots Flash. Story Tweet
February 11, 2016 Keeping your Bitcoins in a brain wallet? Maybe not such a good idea as blockchain security just took significant hit. Story Tweet
February 11, 2016  Good News: White Hat Hackers strike again. Story Tweet
Good News: White Hat Hackers strike again. Story Tweet
February 11, 2016 James Clapper, US TopSpy, suggests IoT can be used for a long list of activities. Story Tweet
February 11, 2016 Sparkle updater used by third parties for Apple OS X has vulnerabilities. Over 700 apps use Sparkle. Do you have one? Story Tweet
February 11, 2016  NYPD used Stingrays over 1,000 times between 2008 and mid-2015 without a warrant. New Yorkers with cell phones are being swept up along with crooks. Story Tweet
NYPD used Stingrays over 1,000 times between 2008 and mid-2015 without a warrant. New Yorkers with cell phones are being swept up along with crooks. Story Tweet
February 10, 2016  Good news: With ENCRYPT Act of 2016 Congress acts toward preventing States from requiring encryption back doors. Story Story Started with Blackberry/PGP with many updates Tweet
Good news: With ENCRYPT Act of 2016 Congress acts toward preventing States from requiring encryption back doors. Story Story Started with Blackberry/PGP with many updates Tweet
February 10, 2016 January catchups: Over 1.1 million compromised in 8 incidents. 950,000 compromised at Centene, St. Louis based health care provider can’t find hard drives Story 50,000 tax records lost Ohio/RITA Story 140,000 exposed at Southern New Hampshire University Story 29,324 compromised at Indiana University Health Story 29,156 compromised at St. Luke’s. Story 20,764 exposed at Blue Shield of California Story 28,209 exposed at New West Health Services of Montana Story 15,000 compromised at BaileysOnline.com from Bailey’s Inc. Story Tweet
February 9, 2016  Can you sign away your Freedom of Speech? Is there a gag order on disseminating bad news? Sadly, yes. Restore your right to bitch (truthfully) about dreck! Story Tweet
Can you sign away your Freedom of Speech? Is there a gag order on disseminating bad news? Sadly, yes. Restore your right to bitch (truthfully) about dreck! Story Tweet
February 9, 2016  “Running Fred” was a pleasant game until unscrupulous developers turned it into something akin to the Running Dead, zombies that will never, ever stop terrorizing your life, won’t ever truly die and operate faster than we can. Story Tweet
“Running Fred” was a pleasant game until unscrupulous developers turned it into something akin to the Running Dead, zombies that will never, ever stop terrorizing your life, won’t ever truly die and operate faster than we can. Story Tweet
February 8, 2016  29,000 FBI & DHS personnel exposed. Was it a hack or not? Story Update Tweet
29,000 FBI & DHS personnel exposed. Was it a hack or not? Story Update Tweet
February 8, 2016 5 articles on exploits that affected an unknown number of people. Nothing spreads a virus like a Trane! A cautionary tale of an internet connected device with a bug, a lack of response from the manufacturer, and a lack of easy updates. Story ATM cards with rollback, use over, and over, and over … Story TMZ joins the unhappy group of real companies whose revenue comes partly from malvertising. How profitable is it? Is the company responsible for malware served up by that company web host? Where is the balance? Story Survey Says: You’ve been scammed. You get an email from a big name asking for your help and feedback. Are you really taking a survey or are you being socially manipulated into providing information to a crook? Story T9000 cyber espionage system, what it learns about you (and tells its boss) is … unsettling. Story Tweet 1of2 Tweet 2of2
February 8, 2016 Many information items. Good News: Dyre trojan operators – BUSTED! Story Ounce for ounce your smartphone is more valuable than silver. Do you protect it? Does it have things you really don’t want on it? Story We can’t counter all unknown threats with known solutions. Read about a change in orientation to proactively create prevention without, or before, detection. Story Sometimes you don’t have to steal money to take it. Story Apple iOS9 users beware “WiFi Assist” default setting. Story Don’t get your strings pulled by an urgent call from “the police”. Story Tweet 1of2 Tweet 2of2
February 7, 2016 Apple iOS8&9 users beware! LockScreen? What LockScreen? A bypass not hard to do if you can get brief physical access. Story Tweet
February 7, 2016 Three information items Tweet How & Vote! How does malware get into Google Play Store? Vote on presentations for RSA 2016 before 2/9/2016!
Story Arbitration pendulum swings. Back in December 2015 we wrote about how the Supreme Court upheld the inclusion of mandatory arbitration effectively stripping smaller plaintiffs from forming class actions. Story Update: eBay will fix bug, at least partly. Story
February 6, 2016 three information items Tweet eBay has a vulnerability allowing attackers bypass a key restriction that prevents user posts from pushing JavaScript code to be executed on end-user devices. eBay has no plans to fix it. Story TaxSlayer and TaxAct, both tax preparation software companies, reported unusual activity involving their customers. Not a breach, apparently attempts using user names and passwords obtained in other ways. Story C&C server for nasty banking trojan Dridex was itself hacked to deliver anti virus softwware instead. Much appreciated! Probably still not legal. Story
February 5, 2016  An iPhone6 with third party repairs may function fine until the iOS9 update which detects the repairs and turns the iPhone6 into a very expensive brick from which there is no recovery. Per Apple this is a “security related feature”. Story Tweet
An iPhone6 with third party repairs may function fine until the iOS9 update which detects the repairs and turns the iPhone6 into a very expensive brick from which there is no recovery. Per Apple this is a “security related feature”. Story Tweet
February 5, 2016  Netgear routers found vulnerable two different ways that can compromise your network and attached devices. Story Tweet
Netgear routers found vulnerable two different ways that can compromise your network and attached devices. Story Tweet
February 4, 2016 Update. “Every step you fake”, how wearables can endanger you or fake-boost your workouts. A study from a Canadian non-profit organization shows how smartwatch apps expose usernames and passwords and can be packed with fake data to lower insurance rates. Story Tweet
February 4, 2016  63,000 exposed at the University of Central Florida including employees back to the 1980s. How the breach was discovered was not disclosed. Story Tweet
63,000 exposed at the University of Central Florida including employees back to the 1980s. How the breach was discovered was not disclosed. Story Tweet
February 4, 2016 Recycled UserID and passwords expose 20 million in Taobao, China’s Amazon-like consumer-to-consumer marketplace. Story Tweet
February 4, 2016  WordPress developers – major surge in malware being delivered to your visitors. Read this now and pass it on to your hosting company. Story Tweet
WordPress developers – major surge in malware being delivered to your visitors. Read this now and pass it on to your hosting company. Story Tweet
February 3, 2016  Tweet Founder of Liberty Reserve alternative currency: Guilty of Money Laundering. Story Silk Road / Bitcoin Swiper re-arrested before he can flee to non-extradition country. Story Mass SMS spammer taking a multi year “vacation” in prison. Story
Tweet Founder of Liberty Reserve alternative currency: Guilty of Money Laundering. Story Silk Road / Bitcoin Swiper re-arrested before he can flee to non-extradition country. Story Mass SMS spammer taking a multi year “vacation” in prison. Story
February 3, 2016  Engine and airframe maintenance information for the very expensive F-35 Joint Strike Fighter can’t be accessed because US Cyber Command requires better security than the Lockheed Martin database provides. Story Tweet
Engine and airframe maintenance information for the very expensive F-35 Joint Strike Fighter can’t be accessed because US Cyber Command requires better security than the Lockheed Martin database provides. Story Tweet
February 3, 2016 Update to the December 2015 Safeway compromise. Would you recognize this as a point-of-sale (POS) terminal as a rigged with a skimmer? Story Tweet
February 3, 2016 Building environment systems can be portals for hackers. Story Tweet
February 3, 2016 Update to SCADA selfies. More examples including guide to Stuxnet. Story Tweet
February 3, 2016 Update to 12/17/2015 Landry’s breach: Affected 46 Landry brands at 350 locations in 34 states, Washington DC and Canada. Some info, not enough. Story Tweet
February 2, 2016

Drone Hunting Eagles
and
Air Launched Canine Missiles
Truly we are embracing the wealth of experience nature has provided.
These Stories Tweet
February 2, 2016  More devices aimed at children and that use the internet were found by someone other the company to leak information that can be used to track kids or read communications. Both companies were responsive, but how, in early 2016 are such vulnerabilities still being delivered to consumers? Story Tweet
More devices aimed at children and that use the internet were found by someone other the company to leak information that can be used to track kids or read communications. Both companies were responsive, but how, in early 2016 are such vulnerabilities still being delivered to consumers? Story Tweet
February 1, 2016  Update: A well researched and presented counterpoint to a “national need for backdoors to encryption”. This update One start to the story Tweet
Update: A well researched and presented counterpoint to a “national need for backdoors to encryption”. This update One start to the story Tweet


