
March 31, 2016 Investigative reporter finds 60+ actions in 20+ states that attempt to compel tech companies with the All Writs Act not only for terrorism, but other underling charges. Some made “under seal” and away from watchful eyes. Just this once? Not. This Update Start of the Story Tweet
March 31, 2016 US State Department Visa & Passport database exposes 500 million records including biometric identifiers. Worse: hackers could alter data allowing for issuance of passports and visas that would otherwise be denied. Story Tweet
March 29, 2016  University of California students, staff and faculty were placed under electronic surveillance without notice by … the University of California. “Academic freedom” in the home of Silicon Valley and Berkely? What happened? Story Tweet
University of California students, staff and faculty were placed under electronic surveillance without notice by … the University of California. “Academic freedom” in the home of Silicon Valley and Berkely? What happened? Story Tweet
March 29, 2016  Marshals Service Scam Widens. Bulletin issued and guidance on what to do if you get the call. Step 1) Remain Calm. Step 2) Remain Calm. This Update Start of the Story Tweet
Marshals Service Scam Widens. Bulletin issued and guidance on what to do if you get the call. Step 1) Remain Calm. Step 2) Remain Calm. This Update Start of the Story Tweet
March 29, 2016 One way to defeat the Apple passcode counter, but did anyone try it? Also – some words from a self described tin-foil-hat conspiracy theorist. This Update Start of the Story Tweet
March 28, 2016  DOJ will seek to dismiss case against Apple Computer stating that the San Bernardino iPhone was cracked without their assistance. No word on the information, if any, was obtained from the phone. This Update Start of the Story Flash Tweet Tweet
DOJ will seek to dismiss case against Apple Computer stating that the San Bernardino iPhone was cracked without their assistance. No word on the information, if any, was obtained from the phone. This Update Start of the Story Flash Tweet Tweet
March 24, 2016 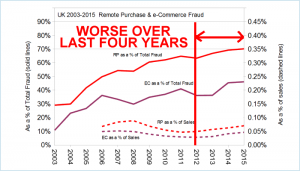 UK Payment Cards Industry Fraud Analysis. Summary: Has gotten worse in both absolute value and relative to sales. Story Tweet
UK Payment Cards Industry Fraud Analysis. Summary: Has gotten worse in both absolute value and relative to sales. Story Tweet
March 24, 2016  Victory for consumers! Four years after 31,800 people were compromised by a health care provider a class action lawsuit was settled in their favor. This Update Start of the Story Tweet
Victory for consumers! Four years after 31,800 people were compromised by a health care provider a class action lawsuit was settled in their favor. This Update Start of the Story Tweet
March 24, 2016 Update to large number of breaches unreported to the public or Congress. Damn Dam attackers indicted, but unlikely to ever appear in court. This Update Start of the Story Tweet
March 23, 2016  Another hospital reverts to 1970 after being compromised by ransomware. What happened, what you can do to prevent a catastrophic impact and discussion on paying or not. Story Tweet
Another hospital reverts to 1970 after being compromised by ransomware. What happened, what you can do to prevent a catastrophic impact and discussion on paying or not. Story Tweet
March 23, 2016  Keyless car fob range extended by crooks. Now the cars can be stolen without a scratch! Vulnerability known since 2011 ignored by auto manufacturers. Will keyless add to insurance premium? Story Tweet
Keyless car fob range extended by crooks. Now the cars can be stolen without a scratch! Vulnerability known since 2011 ignored by auto manufacturers. Will keyless add to insurance premium? Story Tweet
March 23, 2016  Amnesty International released report citing encryption as necessary to the support of human rights and that forced backdoors are antithetical to those rights. This Update Start of the Story Tweet
Amnesty International released report citing encryption as necessary to the support of human rights and that forced backdoors are antithetical to those rights. This Update Start of the Story Tweet
March 23, 2016  What was the new support that might crack the San Bernardino iPhone and bring an end to the DOJ/FBI attempts to use the All Writs Act to compel Apple? Might be a renouned security company in Israel. This Update Start of the Story Tweet
What was the new support that might crack the San Bernardino iPhone and bring an end to the DOJ/FBI attempts to use the All Writs Act to compel Apple? Might be a renouned security company in Israel. This Update Start of the Story Tweet
March 23, 2016 Verizon Customers – were you informed that personal information on 1,500,000 of you is up for sale? Story Tweet
March 22, 2016  Real time video face alteration casts doubt on the truth of what we see. What the eyes see and the ears hear, the mind believes. Harry Houdini Master Illusionist. Story Tweet
Real time video face alteration casts doubt on the truth of what we see. What the eyes see and the ears hear, the mind believes. Harry Houdini Master Illusionist. Story Tweet
March 21, 2016 DOJ requests delay the day before Judge Pym was to reconvene in USA vs Apple Computer. Why? May have to do with new vulnerability announced earlier today. This Update Start of the Story Tweet
March 21, 2016 Professor & students find new vulnerability in Apple iOS. Decidedly non-simple to exploit its appearance has disturbing impact on user security, but may provide a counter to the DOJ claim that the All Writs Act (AWA) is the only way. This Story Update to the AWA Story Start of the AWA Story Tweet
March 21, 2016 Inspector general finds major weaknesses in Veteran’s Administration Information Technology and Security for the 16th straight year. VA wants to double their cyber security budget to fix the problems within two years from the inspection. Story Tweet
March 21, 2016 Companies that allow bring your own device (BYOD) need to secure their information systems in a manner different than protection from company owned devices. Story Tweet
March 21, 2016 What country is the clear leader in getting bug bounties from Facebook since 2011? White hat hackers rule in India! Story Tweet
March 21, 2016 FBI NHTSA create public service announcement on protecting your car computers from hacking. Sounds like protecting your phone. Story Tweet
March 20, 2016  ProtonMail ends 2 year beta and opens doors with end-to-end encryption for all. What they don’t have governments can’t get. Story Tweet
ProtonMail ends 2 year beta and opens doors with end-to-end encryption for all. What they don’t have governments can’t get. Story Tweet
March 20, 2016 Use of the ‘secure’ in https measured and disclosed by Google for Google services and other domains. You might be surprised by what is and isn’t secured. Story Tweet
March 19, 2016  Ever wonder what the some federal agencies know about you or grandpa? Don’t want to fill in all the forms? As a public service some folks have created a site to generate the forms. You still have to sign ’em and mail ’em, but you won’t get writers cramp doing it. Story Tweet
Ever wonder what the some federal agencies know about you or grandpa? Don’t want to fill in all the forms? As a public service some folks have created a site to generate the forms. You still have to sign ’em and mail ’em, but you won’t get writers cramp doing it. Story Tweet
March 19, 2016 Security researcher investigating Bangladesh Central Bank $81M e-heist (attempted $1B) goes missing. This Update Start of the Story Tweet
March 19, 2016 Small merchants who have EMV terminals face long delays in getting certified. They have no recourse except to wait while paying rising losses and interchange fees that include loss expense participation. So, two small merchants are suing and pursuing class-action status. This Update Start of EMV Story Tweet
March 18, 2016  Apple fires some criticism at the Department of Justice in another legal filing prior to the hearing scheduled for next Tuesday. Several interesting points about prior senior intelligence personnel taking the position that we are safer with strong encryption. This Update Start of the Story Tweet
Apple fires some criticism at the Department of Justice in another legal filing prior to the hearing scheduled for next Tuesday. Several interesting points about prior senior intelligence personnel taking the position that we are safer with strong encryption. This Update Start of the Story Tweet
March 18, 2016  Android Users: Beware! StageFright has spawned an evil new variant Metaphor. To be compromised just watch a cute video for 15 seconds. Story Tweet
Android Users: Beware! StageFright has spawned an evil new variant Metaphor. To be compromised just watch a cute video for 15 seconds. Story Tweet
March 18, 2016 Major chip in ‘droid & IOT devices has severe vulnerabilities. Patches for affected phones are in the pipeline. Some IOT devices don’t get updates at all. Story Tweet
March 18, 2016 The consequences of identity theft get an information security professional arrested, at home, in front of his kids, for crimes committed by his identity. What happened before, after and how to prevent it from having that impact on you. Story Tweet
March 17, 2016 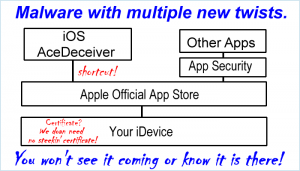 AceDeceiver for Apple devices, malware bypasses code review, enters AppStore, avoids all certificate controls, infects non-jailbroken devices and … you want more from a wallpaper app? Story Tweet
AceDeceiver for Apple devices, malware bypasses code review, enters AppStore, avoids all certificate controls, infects non-jailbroken devices and … you want more from a wallpaper app? Story Tweet
March 17, 2016 State of the Phish report – trends including impacts, costs, effectiveness, effect of personalization, sucker rate by industry, common protection types, and more. Story Tweet
March 17, 2016 Steam powered gaming: 77k accounts hacked per month by over 1200 Trojan groups that compromise accounts and steal game items that cost real money. This Update Start of the story Tweet
March 16, 2016  Massive Malvertising served from major web sites over the weekend. Angler exploit exposed many. Some web sites want you to drop your ad-blocker? “Just trust us” I do, but do I trust everyone you trust? Story Tweet
Massive Malvertising served from major web sites over the weekend. Angler exploit exposed many. Some web sites want you to drop your ad-blocker? “Just trust us” I do, but do I trust everyone you trust? Story Tweet
March 16, 2016 The inherent danger in the internet of things reaches to every room in the house and every connected device as aptly demonstrated at a recent press conference. (R-rated for explicit sex toy reference) Story Tweet
March 16, 2016 Update: Attempted theft of $1B from the Bangladesh Central Bank used internal messaging technology and appear to be fully authorized. May have been a breach from the outside or an inside job. Most funds stopped from leaving bank thanks to alert employees at intermediary banks (see start of story). $81M gone, 1 resignation, 3 fired. This Update Start of the Story Tweet
March 16, 2016 Misconceptions on the debate between personal privacy and a surveillance state. How cybersecurity deliberately weakened by government act came back to expose much to our enemies. Good discussion. This Update Start of the Story Tweet
March 16, 2016 Can someone with a tablet and skills open the blinds in your hotel room? Turn on the lights or open your door? Yes, if you’re in a place that used an old protocol without any authentication. Story Tweet
March 15, 2016 Florida Sheriff Judd will lock up that “rascal” Tim Cook, CEO of Apple if he won’t unlock an iPhone for him. We admire the clear presentation of intent but … Story Tweet
March 15, 2016  Crooks convert a charge card reader at a convenience store into a skimmer that works for them. All in just three seconds. Story Tweet
Crooks convert a charge card reader at a convenience store into a skimmer that works for them. All in just three seconds. Story Tweet
March 15, 2016 Apple vs FBI, the timing. Other encryption services currently operating. Futility of trying to curb encryption use when 2/3 of the products are from outside the US. A US Senator changes their mind in public. This Update Start of the Story Tweet
March 15, 2016 Apple head of services worried that the next step is to compel Apple to remotely turn on camera and microphone of iPhones. The capability already exists. Where does privacy end? Story Tweet
March 15, 2016 President’s Speech at SXSW and a response from a presidential candidate. This Update Start of the Story Tweet
March 15, 2016  Update to the Marshals scam. Why it was so effective and what you should try to remember if this happens to you. This Update Start of the Story Tweet
Update to the Marshals scam. Why it was so effective and what you should try to remember if this happens to you. This Update Start of the Story Tweet
March 15, 2016 Locky update: New infection method (Word doc with macros no longer required) and a major increase in volume powered by the Dridex ‘bot network. This Update Start of the Story Tweet
March 15, 2016  That cute image with sparkly noise can be part of a cyber security threat. The “noise” can be source code for malware, ready to be extracted with a snippet of code and infect your computer. Story Tweet
That cute image with sparkly noise can be part of a cyber security threat. The “noise” can be source code for malware, ready to be extracted with a snippet of code and infect your computer. Story Tweet
March 15, 2016 Your anti virus software is “certified” and that justifies the higher price tag for the superior protection. Are you sure? What does “certified” mean? Sometimes not so much. Story Tweet
March 14, 2016  Ever been called by the US Marshals Service and told they’re coming for you? It would have been a first for me, but my nose saved me. Story Tweet
Ever been called by the US Marshals Service and told they’re coming for you? It would have been a first for me, but my nose saved me. Story Tweet
March 14, 2016  Update on the DROWN vulnerability. Knowing is half the battle. Seems we’re not winning the other half any time soon. This Update Start of the Story Tweet
Update on the DROWN vulnerability. Knowing is half the battle. Seems we’re not winning the other half any time soon. This Update Start of the Story Tweet
March 13, 2016  October 2013 Oracle: Java problem fixed. March 2016: Umm, no it wasn’t and millions are still vulnerable. Story Tweet
October 2013 Oracle: Java problem fixed. March 2016: Umm, no it wasn’t and millions are still vulnerable. Story Tweet
March 12, 2016  A person not a direct party to the ongoing battle between the DOJ/FBI has provided support friendly to Apple and hopefully of interest to the court as to official statements already submitted. This Update Start of the Story Tweet
A person not a direct party to the ongoing battle between the DOJ/FBI has provided support friendly to Apple and hopefully of interest to the court as to official statements already submitted. This Update Start of the Story Tweet
March 11, 2016  FBI/DOJ files response to Apple in San Bernardino case. Interesting reading for the strong of stomach. This Update Start of the Story Tweet
FBI/DOJ files response to Apple in San Bernardino case. Interesting reading for the strong of stomach. This Update Start of the Story Tweet
March 11, 2016 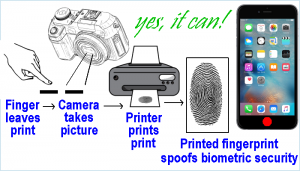 Simplest way we know to defeat fingerprint biometric security on cell phones. Requires digital image of print (not even a great picture), a color inkjet printer, some commercially available paper and presto! Story Tweet
Simplest way we know to defeat fingerprint biometric security on cell phones. Requires digital image of print (not even a great picture), a color inkjet printer, some commercially available paper and presto! Story Tweet
March 11, 2016 2.2 million exposed during breach of 12st Century Oncology more than five months ago. Story Tweet
March 11, 2016 Irony: “High security” web hosting company knocked off line by DDoS attack and apparently hacked exposing customer information including charge cards. Insult: along with public links to company information the hackers posted what not to do when running a “high security” hosting company. Story Tweet
March 11, 2016 Alert bankers stop almost one billion US dollars in multiple transfers from a nation’s central bank. Good nose! Story Tweet
March 10, 2016  Disillusioned member brings trove of information on 22,000 ISIS member. Story Tweet
Disillusioned member brings trove of information on 22,000 ISIS member. Story Tweet
March 10, 2016 Bad News: Tyupkin malware (ATM jackpotting, updated to new version “GreenDispenser”) breaks jail. Story Tweet
March 10, 2016  You get a parking ticket with a nice quick recognition code to scan for payment or protest. Do you scan it? Story Tweet
You get a parking ticket with a nice quick recognition code to scan for payment or protest. Do you scan it? Story Tweet
March 10, 2016 Searching the internet for “how to hack facebook”? Beware else you wind up being the one hacked. Someone did find a large, gaping security hole, and bravo to FB for closing it quickly. Story Tweet
March 10, 2016  Telematics (GPS, speed etc) for hundreds of trucks were found to be insecure using 40+ year old software. Story Tweet
Telematics (GPS, speed etc) for hundreds of trucks were found to be insecure using 40+ year old software. Story Tweet
March 09, 2016  A weak security measure was targeted and compromised by crooks victimizing people twice. The IRS has stopped issuing IP-PINs. Targeted Story Stopped Story Tweet
A weak security measure was targeted and compromised by crooks victimizing people twice. The IRS has stopped issuing IP-PINs. Targeted Story Stopped Story Tweet
March 09, 2016  Converting some bad hackers into white hats. If you can’t beat ’em hire ’em! Story Tweet
Converting some bad hackers into white hats. If you can’t beat ’em hire ’em! Story Tweet
March 09, 2016  You think you have a cyber security problem? How about 300 million hits a day? ouch! Story Tweet
You think you have a cyber security problem? How about 300 million hits a day? ouch! Story Tweet
March 08, 2016 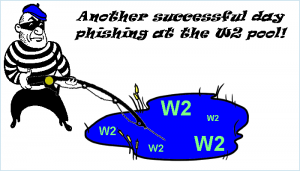 Another company gets a fake email from a “senior official” and sends off a print of W2 information for current and former employees. Story Tweet
Another company gets a fake email from a “senior official” and sends off a print of W2 information for current and former employees. Story Tweet
March 08, 2016  Wendy’s confirms breach. Number affected remains unknown. Credit unions hit hard and fast with related debit card fraud. This Update Start of the Story Tweet
Wendy’s confirms breach. Number affected remains unknown. Credit unions hit hard and fast with related debit card fraud. This Update Start of the Story Tweet
March 08, 2016 DOJ Appeals Judge Orenstein’s ruling denying the requested application of the All Writs Act in New York. Story Tweet
March 07, 2016  A fully capable ransomware targets Macs. Introduced as a Rich-Text-Format document, part of a legitimate application installer. Signed by valid Apple developer certificate. Story Tweet
A fully capable ransomware targets Macs. Introduced as a Rich-Text-Format document, part of a legitimate application installer. Signed by valid Apple developer certificate. Story Tweet
March 06, 2016  In the boxing match that pits a surveillance state vs personal privacy in one corner stands the Attorney General and the FBI. In the other, the Secretary of Defense, the Secretary of State, the UN Commissioner for Human Rights, Apple, Google, AT&T and more. This Update Start of the Story Tweet
In the boxing match that pits a surveillance state vs personal privacy in one corner stands the Attorney General and the FBI. In the other, the Secretary of Defense, the Secretary of State, the UN Commissioner for Human Rights, Apple, Google, AT&T and more. This Update Start of the Story Tweet
March 06, 2016  Seagate scammed out of W2 information for current and former employees in the same email spear phishing attack that speared SnapChat, but not others. Story Tweet
Seagate scammed out of W2 information for current and former employees in the same email spear phishing attack that speared SnapChat, but not others. Story Tweet
March 05, 2016 Four stories Tweet Update on breach under reporting at law firms Story Irony strikes at RSA security conference Story Clickjacking – misusing accessibility tools to get users to allow malware. Story Oh no Dwolla, didn’t! Story
March 04, 2016
 Smartphones hacked by listening to radiation and power level changes to extract signing keys from Elliptic Curve Digital Signature Algorithm (ECDSA) used in many applications such as Bitcoin wallets, Apple Pay, OpenSSL, CoreBitcoin, iOS and more Story Tweet
Smartphones hacked by listening to radiation and power level changes to extract signing keys from Elliptic Curve Digital Signature Algorithm (ECDSA) used in many applications such as Bitcoin wallets, Apple Pay, OpenSSL, CoreBitcoin, iOS and more Story Tweet
March 04, 2016 Amazon rips crypto from appliance and screw the people who were using it. Story Tweet
March 04, 2016  UK Crown Prosecution Service published for public comment laws catching up to social media crimes. [ anyone in US paying attention? ] Story Tweet
UK Crown Prosecution Service published for public comment laws catching up to social media crimes. [ anyone in US paying attention? ] Story Tweet
March 04, 2016  Modern day sea pirates combine the historical tactics of their swashbuckling heyday and adopt some modern technology concepts. Story Tweet
Modern day sea pirates combine the historical tactics of their swashbuckling heyday and adopt some modern technology concepts. Story Tweet
March 03, 2016  Multiple legacy crypto weaknesses can now be exploited. An unintended byproduct of government influence and an argument against backdoors, deliberate, or like this. Story Tweet
Multiple legacy crypto weaknesses can now be exploited. An unintended byproduct of government influence and an argument against backdoors, deliberate, or like this. Story Tweet
March 02, 2016  A 1984 Supreme Court case and the 1994 Communications Assistance for Law Enforcement Act skewer Department of Justice attempt to use All Writs Act to bypass inconvenient law. This Update Start of the Story Tweet
A 1984 Supreme Court case and the 1994 Communications Assistance for Law Enforcement Act skewer Department of Justice attempt to use All Writs Act to bypass inconvenient law. This Update Start of the Story Tweet
March 02, 2016 US smartphone market penetration rises for fourth straight quarter approaching 80%. Story Tweet
March 02, 2016 Multiple updates on surveillance vs privacy embodied in Apple v FBI. Did the Department of Justice skip a step? This Update FBI Director asks: What if Apple engineers are kidnapped? This Update Proposed foreign legislation on forcing manufacturers to crack their own phone. This Update Start of the Story Tweet
March 02, 2016 McAfee Labs published a five year look ahead for threats against hardware, ransomware, payment systems, via and against cloud services, wearable technology, automobiles, cyber espionage, hacktivism, and more. Story Tweet
March 1, 2016  Apple wins in New York as judge declined late yesterday to force them to comply with All Writs Act. This update Start of the Story Tweet
Apple wins in New York as judge declined late yesterday to force them to comply with All Writs Act. This update Start of the Story Tweet
March 01, 2016 Catch up on seven stories from February we couldn’t get to in time. Tweet
“Locky” Ransomware Story
CTB Ransomware attacks websites Story
Twitter password recovery bug exposed 10k. Story
Is your wireless printer exposing your network? Story
Police brew and refine their own surveillance trojan Story
TOR hacked by US University under DOD contract? Story
MouseJacking, not a joke, a cheaply mounted attack you don’t want to receive. Story


