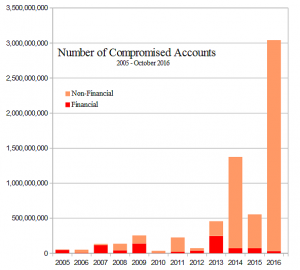
History of Compromises 2005 to October 2016
Biometric Identification EMV NFC RFID
Credit Cards vs Debit Cards
Credit Freeze or Monitoring?
Skimmers: ATM & POS Cell Phones
Cars: How many ways can your car get hacked?
Have I been compromised?
When do you get told?
You’re been compromised! Now what?
Ever Wonder How Your Card Was Compromised?
The Fifth Amendment as it relates to biometrics
How do you know you’ve been breached?
Who loses when companies suffer a cyber heist?
UK Payment Industry Fraud 2003-2015
The Quick Recognition (QR) Code
Global economy
Twitter Index
Thermal Paper Pollution
NC3, The next step in the evolution of commerce
History of compromises
Compromises during the current year
Details and summaries of compromises by year from 2005
October 2016 was the last month of detailed breach gathering. Read why.
| From 2005 to 10/31/2016 Total Accounts Compromised By Type |
||
| 829,195,839 | 13.0% | Financial |
| 5,549,695,177 | 87.00 | Non-Financial |
| 6,378,891,016 | 100.00% | |
| Total Incidents By Type | ||
| 263 | 3.74% | Financial |
| 4,074 | 58.02% | Non-Financial |
| 2,685 | 38.24% | Unknown |
| 7,021 | 100.00% | |
2016 had massive breaches affecting twice 2014, the previous worst year
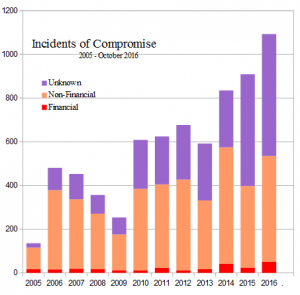
October 2016 was the last month of detailed breach gathering. Read why.
Ever Wonder How Your Card Was Compromised?
You’ve been told your card was compromised. Ever wonder what really happened? Think you can find out? Read this article from KrebsOnSecurity where noted security researcher Brian Krebs describes some common forms of fraud, their distinguishing characteristic(s) and the chances that you’ll ever learn where and how your account was compromised.
The most common form was a “hacked main street merchant, restaurant: Most often powered by malicious software installed on point-of-sale devices remotely. Distinguishing characteristic: Most common and costly source of card fraud. Losses are high because crooks can take the information and produce counterfeit cards that can be used in big box stores to buy gift cards and/or expensive goods that can be easily resold for cash. Chances of consumer learning source of fraud: Low, depending on customer card usage.”
So, if the confidential consumer credentials were never held by the merchant (not even for a moment so POS RAM scrapers have nothing to scrape), yet the merchant gets paid and the consumer gets billed, then the most common and costly source of card fraud would become profitless for crooks. Sounds like a good idea for a new concept in charge cards. Yep, it is the core of the NoCompromiseChargeCard (NC3).
Return to top
Global Economy
Charge cards are vital to our national and global economy, which means more opportunities for everyone – including criminals. (4 page PDF)
Return to top
Thermal Paper Pollution
IEEE article, see abstract Reference for 22.87 million pounds In commercial use since the mid-1950s Bisphenol A (BPA) is an organic compound found in some plastics and in the epoxy resins used some coatings of food and drinks cans. It was recently found to also exist in the paper for cash or charge card processors using thermal printing paper. See Phys.Org article Reference for containing BPA
Return to top
The Quick Recognition (QR) Code
‘QR Code’ is a registered trademark of Kabushiki Kaisha Denso (Denso Wave Incorporated) and is used with permission
Return to top
You’ve been compromised! Now What?
There are Three Major Credit Bureaus and this Federal Deposit Insurance Company (FDIC) web site provides you information on how to contact them to ask about or obtain your credit report or credit score, alert creditors to a possible fraud using your name, or for any other reason. In early 2016 the Federal Trade Commission (FTC) launched a new consumer tool IdentityTheft.Gov
Then read this article by security researcher Brian Krebs about freezing your credit status and opting out of credit offers that can be intercepted by crooks. If you were the victim of tax fraud, read this KOS article. Also see the Identity Theft Resource Center for victim assistance, consumer information and more.